cd ..
EN
Networking
🔥 The most common bad practices in firewall rules (and how to avoid disaster)
R
Rodolfo Echenique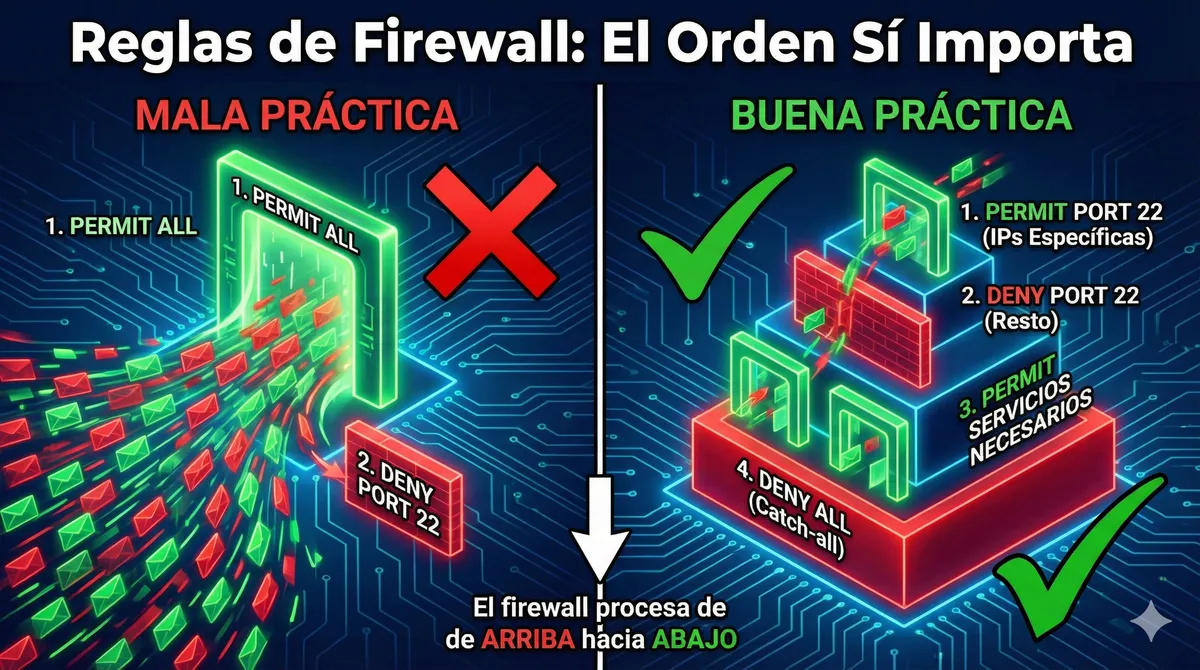
Automated Translation: This article was originally written in Spanish and translated by Gemini AI.
In the world of network administration, few things are as critical—and as underestimated—as the correct configuration of firewall rules. Many administrators (or over-permissive enthusiasts) have the mistaken idea that it is enough to put permit rules at the top and block rules at the bottom. Unfortunately, that logic is dangerous.
📜 The firewall doesn't interpret intentions, it interprets orders
Firewalls process rules from top to bottom, and apply the first rule that matches the traffic. Period. No interpretation, no second chances. This implies two things:
- 👉 If you place a very generic block rule at the top, you might break things without realizing it.
- 👉 If you permit something too broad first, any subsequent rule intended to restrict it will no longer take effect.
❌ Classic example of bad practice
1. PERMIT ALL
2. DENY port 22 from unknown IPs
🔎 Result: Rule 2 is never met. Why? Because the first rule already allowed everything through. Your SSH port was left open, and you didn't even know it.
✅ What a responsible structure should look like
1. PERMIT port 22 only from specific IPs (offices, VPN)
2. DENY port 22 from the rest
3. PERMIT necessary services with specific rules
4. DENY ALL (final catch-all rule)
This approach ensures that only what you really want is permitted, and everything else is blocked by default. As it should be.
⚠️ What can go wrong if you do it incorrectly?
A lot. For example:
- You might render essential services inoperable and no one will know why.
- You might block your own remote access.
- You might brick the equipment if you don't have local or out-of-band access.
- You might compromise the complete security of your infrastructure.
And if you don't have a backup or alternative access... good luck recovering it.
🧑💻 This job is not for the unprepared
Modifying firewall rules is not “try it and see what happens.” It is a critical task that must be performed with:
- Knowledge of networks, services, and protocols.
- Testing in a controlled environment.
- Disaster recovery plans.
- Secure physical or remote access.
- And above all: experience.
At Central Node, we have specialized professionals in network infrastructure and cybersecurity. We know how to design and implement firewall policies that work and are secure, without compromising the performance of your services or leaving blind spots.
🧷 Golden tip
“If you’re going to play with fire (firewall), at least bring an extinguisher (backup).”
🚀 Want to do it right from the start?
Contact us.
At Central Node, we transform chaos into solid, scalable, and secure infrastructure.
At Central Node, we transform chaos into solid, scalable, and secure infrastructure.